After a long, long wait, and few teases over the past few months, Microsoft has finally released support for establishing a Remote PowerShell session to the Security and Compliance Center via certificate-based authentication. This is enabled as part of the freshly released 2.0.6-Preview5 version of the ExchangeOnlineManagement PowerShell module, and it works pretty much in the same way as CBA connectivity to the Exchange Online endpoint. The accompanying documentation has also been updated, so I will not dig into all the details (plus, I covered CBA connectivity via the ExchangeOnlineManagement module extensively in the past here and here.)
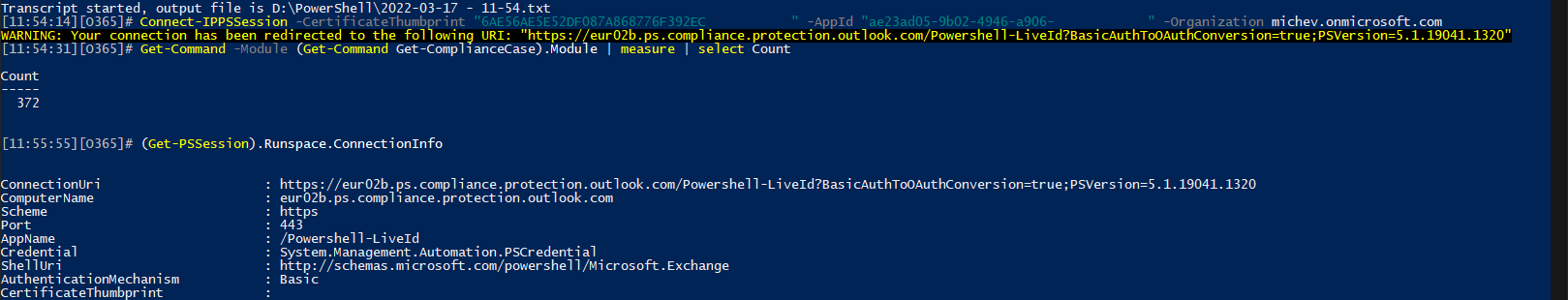
Without further ado, to connect to SCC PowerShell via the new CBA-based method, you need to use the Connect-IPPSSession cmdlet with the –CertificateThumbprint parameter. Of course, make sure all the prerequisites are met, as per the articles linked above (have an app registration with sufficient permissions created, add a certificate credential to it, assign admin roles, download the latest preview version of the module). For example:
Connect-IPPSSession -CertificateThumbprint "AAE56AE4E5DDF0DDA86874AF39254F49FEE623BC" -AppId "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx" -Organization tenant.onmicrosoft.com
With the most permissive role assigned, a total of 372 cmdlets are exposed when connecting via CBA. This is in fact a significant increase over the 328 cmdlets exposed when connecting via other methods, and at this point it’s not clear as to why some of those cmdlets are not available when connecting in a user context. Examples include: Cancel-DlpEdmSession, Create-FilePlanFirstRunLabels, Enable-ComplianceFeature, Start-DlpSensitiveInformationScan and more. Likely some RBAC magic is happening here, but it’s hard to tell due to the limited set of RBAC cmdlets supported for the SCC endpoint.
Other than that, the cmdlets I’ve tested all seem to work as expected, and return the same output as their “user-context” counterparts. I haven’t bothered with all 300+ of course, for obvious reasons. Keep in mind that the module is marked as preview one though, so the occasional issue is to be expected.
Hi Michev,
New-ComplianceSearch Command working fine. But Start-ComplianceSearch command not working if we use certificate based authentication.
I cannot get this to work. I can connect to ExchangeOnline using the CBA, but for IPPSSession it doesn’t seem to work. Can you share what API Permissions you configured in your App Registration? I have the Exchange.ManageAsApp, but I feel like I’m missing something for the Compliance Center or Purview access like Purview.ApplicationAccess? Is that required as well?
FYI, when I attempt to connect, I get prompted to select my login account and then get a “Need admin approval” error. I shouldn’t get a login account selection box at all so I’m not sure what I’m missing.
Thx.
Did you assign a role that allows access to the Compliance/Purview admin center? The list of supported roles is here: https://learn.microsoft.com/en-us/powershell/exchange/app-only-auth-powershell-v2?view=exchange-ps#assign-azure-ad-roles-to-the-application
Not sure about the prompt though. Update to the latest module version and try in a fresh new console window.
Having gone through a similar issue, retrace your steps when it comes to the certificate used for the connection. Make sure that the Thumbprints match in the app and on the local machine. Try using the PFX file / password combination to see if that works instead. If that fails, double-check your process on a jump box or alternate workstation to make sure it isn’t a local issue. Also, as Vasil said, check to make sure you are running the latest version of the Exchange Online Management PS module. Remove any old modules that may be lingering on the workstation as well.
Hi James,
You need to create a service principal object for you Azure app & then assign the ediscovery manager role to it.
Connect-AzureAD
1) $AADApp = Get-AzureADServicePrincipal -SearchString “EXO PowerShell Unattended”
2) New-ServicePrincipal -AppId $AADApp.AppId -ObjectId $AADApp.ObjectId -DisplayName “SP for Azure App EXO PowerShell Unattended”
3) $SP = Get-ServicePrincipal -Identity “SP for Azure App EXO PowerShell Unattended”
Connect to security & compliance Powershell.
4) Add-RoleGroupMember -Identity “eDiscoveryManager” -Member $SP.ObjectId