Hey folks, look at what landed in my Inbox yesterday:
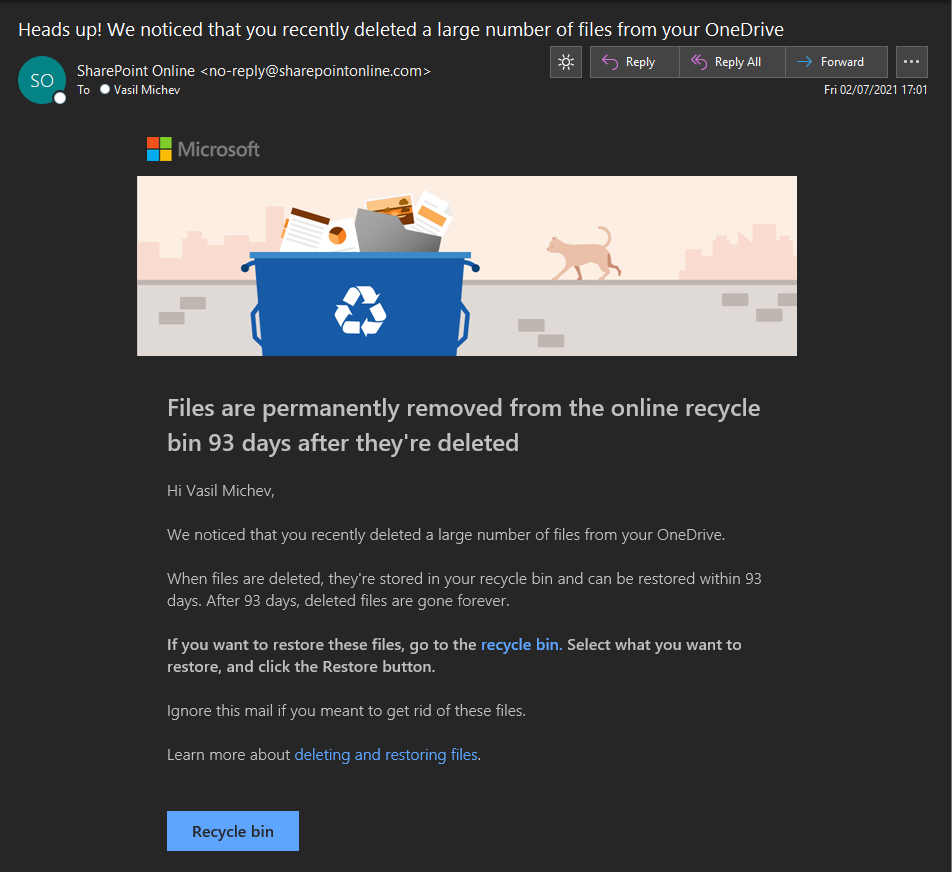 This is not a spam or a clever phishing message, it’s a legitimate email notification sent from SharePoint Online, as one can verify by looking at the headers. So why am I bothering you with this? Because it’s the first time I actually see one of these!
This is not a spam or a clever phishing message, it’s a legitimate email notification sent from SharePoint Online, as one can verify by looking at the headers. So why am I bothering you with this? Because it’s the first time I actually see one of these!
The feature has been available for consumer OneDrive for few years now, and was supposedly introduced to OneDrive for Business/SharePoint Online a while back. Up until today however, I have never even seen such email, although I regularly see the alert policy ones, generated for the same activity. An example is shown below, for the exact same event:
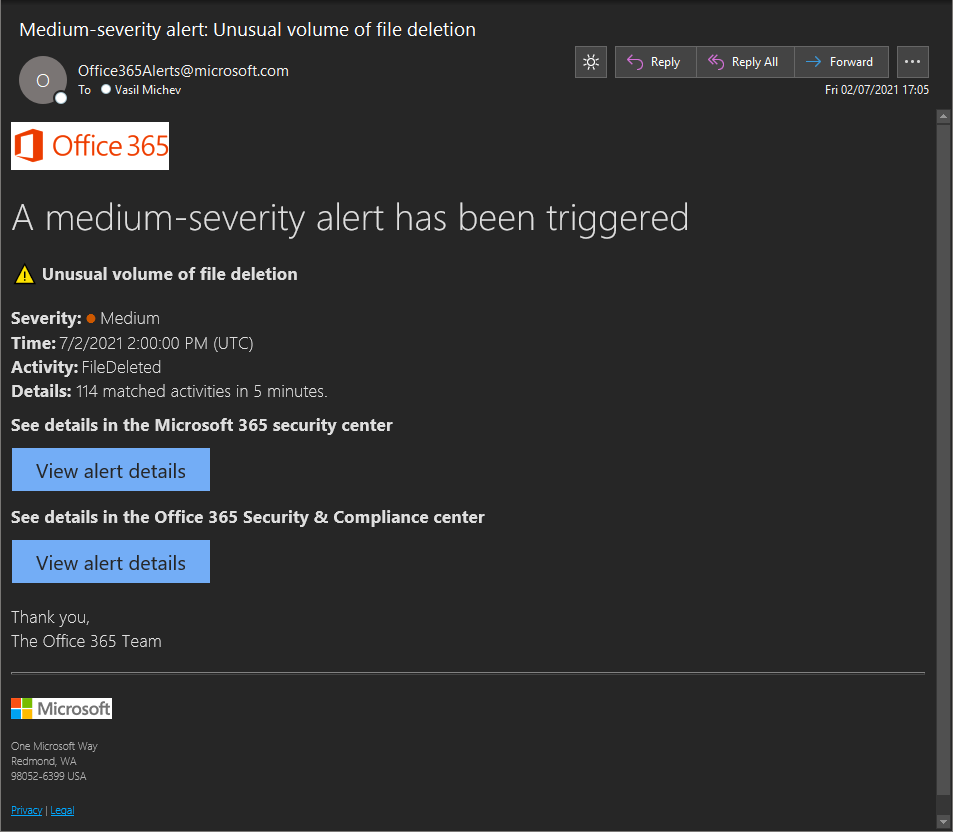 While both notifications are generated for the same action/event, they are not the same thing. The former one, sent from no-reply@sharepointonline.com, is an “end user” notification, is generated for deletions in your own ODFB and sent only to you. No customization settings are available, but if you want to disable those notifications, you can do so by opening your OneDrive > Settings > Notification settings and moving the Email notifications when OneDrive detects lots of files are deleted at once toggle.
While both notifications are generated for the same action/event, they are not the same thing. The former one, sent from no-reply@sharepointonline.com, is an “end user” notification, is generated for deletions in your own ODFB and sent only to you. No customization settings are available, but if you want to disable those notifications, you can do so by opening your OneDrive > Settings > Notification settings and moving the Email notifications when OneDrive detects lots of files are deleted at once toggle.
The alert on the other hand is something you can customize, to an extent, either in the old Security and Compliance Center or the new Microsoft 365 defender portal. It is in fact one of the default alert policies created by Microsoft, which you can find under Policies & Rules > Alert policy. Therein, you can toggle the notifications on or off, change the set of recipients (by default email notifications are sent to all tenant admins), and change the daily limit for such notifications. Or, if you prefer, you can create a similar alert from scratch, by selecting the “deleted file” event as the activity and add additional conditions as needed. For example, you can configure it to fire for events generated by a given user or for files in specific site collection, or even file names, and control how many matches are required before the alert is fired.
The other difference is that the alert policies generate actual alerts, as in entries that you can find under the Alerts section in the SCC/M365 Defender portal (https://security.microsoft.com/alerts). You can classify the alert, assign it to an incident or even browse each individual event that contributed to generating the alert, which in this case includes the full list of files that were deleted. In contrast, the SPO notification is only sent to the end user, and does not generate any alert entry. It also lacks details as to how many files were deleted and where from, and features only a link to the user’s Recycle bin. Which is probably for the best, as we don’t want to overwhelm the user with too many details or scare them.
What’s also interesting is that the SPO notification email was delivered faster compared to the alert one, which makes sense considering the amount of time it usually takes to ingest events into the Unified audit log, to which the alert is tied. Both are of course sent after the actual deletion, so can’t help you from preventing deletions from a bad actor. But being informed about it is still a good thing, so having those notifications hit end users is a step in the right direction. And a good source of helpdesk tickets, I suppose 🙂