A while back I posted a “proof of concept” article/script about enumerating all shared files across your Office 365/OneDrive for Business environment. The script used the Graph API endpoints to get a list of users within your tenant, then for each user checked the presence of a OneDrive “drive”, enumerated the items therein and spilled details for any “shared” file. Sort of like the “sharing” report that you can generate within Office 365, but for all users.
You can apply much of the same code to a different scenario – removing access for any shared files. This is a common task for “leavers” scenarios, where the organization wants to make sure that content of user’s drive will not be accessible anymore by anyone else other than some designated person, be it the user’s manager or someone within the same team or even the legal department. A quick way to achieve this is to play with the sharing permissions on the individual Site collection corresponding to the user’s drive, but where’s the fun in that. Instead, I’ve compiled another “proof of concept” script that will remove sharing permissions from any and all files within given user’s OneDrive for business drive. Kind of like the “stop sharing” button we have for individual items, but applied at the user level.
As before, we will be using the Graph API endpoints, and to start with, we need a valid token. The script uses the application permissions model, so you will need to provide your tenantID, the appID of an Azure AD application you’ve created and the client secret associated with it. The application will need to have the Sites.ReadWrite.All permission in order to be able to enumerate drives, files within them and their permissions, as well as remove the permission entries. Users.Read.All permissions are also necessary, as to perform a check whether the provided user identifier corresponds to an actual user within the tenant.
If a valid drive is found for the user, the script will proceed to enumerate all items within it, depending on the specified parameter values. Unlike the “report” script, this time we will expand folders by default (controlled via the –ExpandFolders switch), up to a depth of two levels (controlled via the –Depth parameter), as to make sure we cover the bulk of the items available within the drive. The last parameter you need to specify is the user against which we will be running the script, via the –User parameter, and provide the value in the form of an UserPrincipalName or GUID. You can also specify the –Verbose switch to spill out additional details during the processing of the drive in question.
Without further ado, you can find the script over at GitHub. Once you have downloaded it, use the following syntax to run it against a given user:
.\Graph_ODFB_remove_all_shared.ps1 -Verbose -User user@domain.com
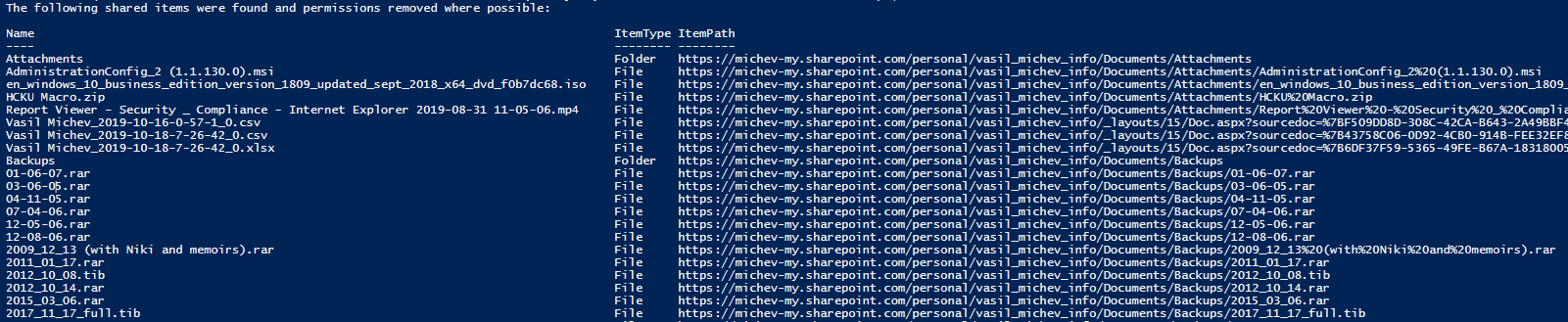
Note that not all permissions can be removed, for example secondary admin for the ODFB site will always keep their access. Here’s also a sample screenshot of the output generated (some improvements are needed there, but I got bored):
If needed, the script can be modified to perform this action for a set or all users within the tenant, but that’s an exercise I’ll leave to the reader. Other improvements that can be made include a more robust error handling, better handling of the output (generating a report?), adding a check whether a file is externally shared and a script parameter to remove just such permissions, etc. Token renewal is something else you might want to take care of, even though it shouldn’t be necessary as we’re handling one user at a time.
Great script for an important task in offboarding of users within an organisation!
Got this working with cert auth which is great, but I noticed an odd behavior when I ran it against myself for testing.
It was going through the Microsoft Teams Chat folder, and started sending me an email saying it was sharing a file with the person it was originally shared to, but when you click the “remove permissions” link in the email it actually did remove them.
It’s like this:
SharePoint App () has shared ‘.xlsx’ with
Do you have any idea why it would be triggering this email?
Hi Mike, who’s sending the email? The script does not have any such logic built into it
A colleague of mine recently found this script and we are using it to find the Everyone claims on all of our ODfB sites. This is great work. Does a similar script exist for all tenant SharePoint sites, excluding ODfB?
Hello. I am getting an error running this script.
Installed PowerShell 7, Microsoft Graph. Basic commands such as Get-MgUser work fine.
Script error:
PS C:\Script> .\Graph_ODFB_remove_all_shared.ps1 -Verbose -User user@contoso.org
ParserError: C:\Script\Graph_ODFB_remove_all_shared.ps1:41
Line |
41 | … script type=”application/json” id=”client-env”>{“locale”:”en”,”featur …
| ~~~~~
| Unexpected token ‘:”en”‘ in expression or statement.
“en” is what is underscored in the error
Thought it might be locale related (as was using a Windows Spanish installation), but got same error on Windows English installation. Windows 10 22H2.
Hope you can help.
Thanks
I would like such a script for removing all shared links on a sharepoint site..
Vasil, We have had this running for a long while (thanks to your previous help), but recently the DELETE command is no longer working to remove permissions, and no errors either. We thought this was related to using the Graph API Beta end point, changed to the v1.0 endpoint but still not working. Any ideas? Thanks again and great work on this script.
Seems to run fine here. Keep in mind that you cannot remove some types of permissions (i.e. inherited ones, Owner permissions, etc), it will mostly remove sharing links.
Hi Vasil, Thank you for the sharing your works. my situation is, I would like to give my staff the ability to remove one person from all his shared files/folder, i.e. one staff run a script and specify a user ID, the script scans all his own OneDrive folders and files to remove the specific user from sharing permission list. upon my studying your script, not a good idea to let general staff know tenantID, appID, or client_secret in plain text. all suggestions are appreciated.
It’s a “proof of concept” script mate, you can replace the authentication part of it with a proper function that handles things in secure manner, say via certificate or Azure Key vault secret…
I have been looking for a script like this for a while. I know this was a lot of work to put together. I have the script logging in but it is not returning any data for any accounts. When I target an account I know has shared folders and files the script returns No shared items. Any ideas? Perms are all correct
It’s almost always permissions 🙂 Best run the script with the verbose switch to see what’s happening.
Thanks. The issue was permissions related, sort of. The app was given SharePoint Sites.ReadWrite.All not graph api Sites.ReadWrite.All access. Once we added graph api Sites.ReadWrite.All all is working. Again Thanks and great work on this script!