It has been a while since I covered what’s new in AzureAD and AzureADPreview module updates, so I figure it’s time for another article. Note that some of these might not be all that new, since my last article on the subject was from April 2019 🙂
The first set of new cmdlets allows us to manage the “staged rollout” feature, as in the per-user switch from federated auth to cloud-only. This feature was first announced at Ignite 2018 and it took Microsoft a while to release the public preview, but it’s finally here. We will cover the feature in more details in another article, for now here are the corresponding PowerShell cmdlets (part of the AzureADPreview module):
| Add-Azure |
Allows an admin to add a group to the cloud authentication roll-out policy in Azure AD. Users in this group will start authenticating to the cloud per policy. |
| New-Azure |
Allows an admin to create the policy for cloud authentication roll-out in Azure AD. |
| Remove-Azure |
Allows an admin to remove the policy for cloud authentication roll-out in Azure AD. |
| Remove-Azure |
Allows an admin to remove a group from the cloud authentication rollout policy in Azure AD. Users in this group will revert back to the authenticating using the global policy (in most cases this will be federation). |
| Set-Azure |
Allows an admin to modify the policy for cloud authentication roll-out in Azure AD. |
Another great new addition are the cmdlets to search the Azure AD Audit and Sign-in logs. Up until now, if we wanted programmatic access to those, we had to use the Graph API. Being able to query the logs directly via PowerShell is appreciated. Unfortunately, I couldn’t get the Get-AzureADAuditSignInLogs cmdlet to work for me, but Get-AzureADAuditDirectoryLogs works just fine:
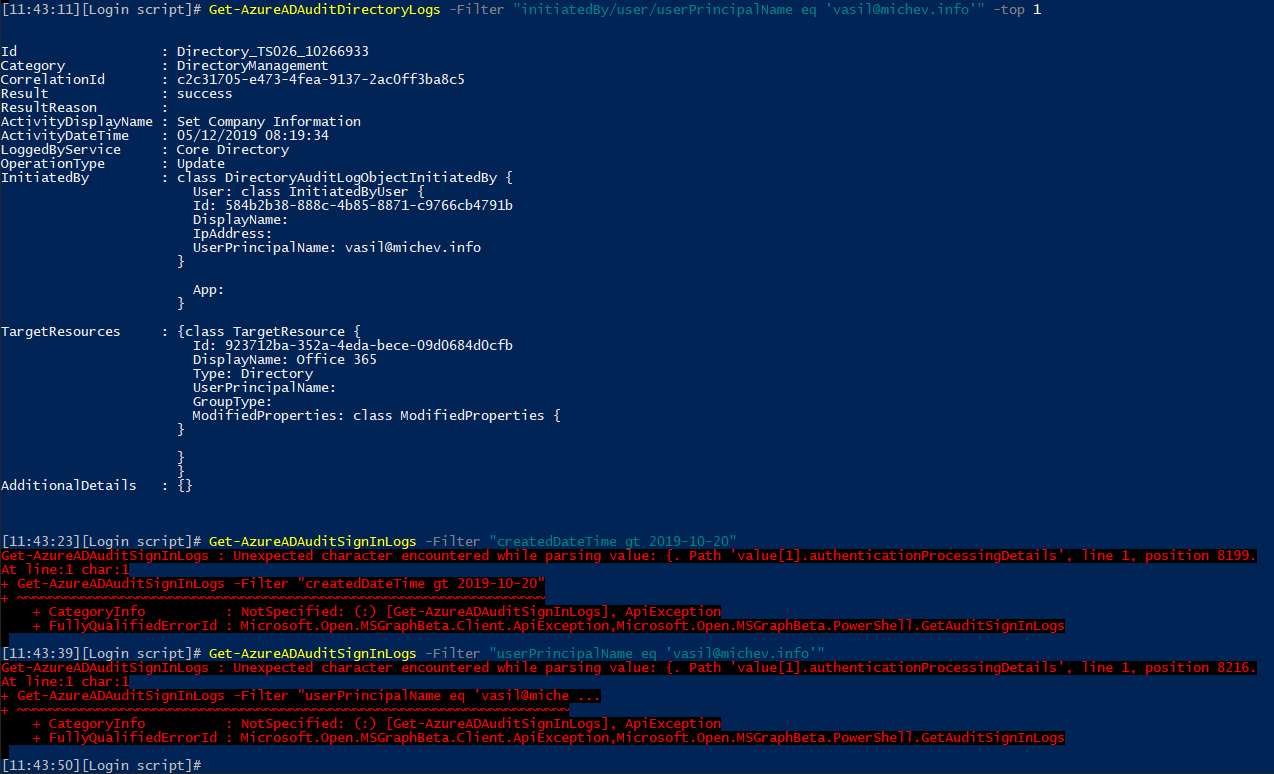 In any case, the two cmdlets are a great addition, and here are the links to their corresponding documentation articles:
In any case, the two cmdlets are a great addition, and here are the links to their corresponding documentation articles:
| Get-Azure |
Get directory audit logs |
| Get-Azure |
Get audit logs of signins |
Another set of cmdlets deals with Role management. The Get-AzureADMSRoleDefinition cmdlet outputs the role definitions of all roles or a given one, and once you have the role ID you can query for any assignments via the Get-AzureADMSRoleAssignment cmdlet. The rest of the cmdlets allow you to create and manage new role definitions and assignments accordingly, with the caveat that only the application-related permissions are currently supported. This functionality has been available for a while in the Azure AD portal and the PowerShell module, but we’re covering it here since we skipped few versions. Here are the rest of the related cmdlets:
| Get-Azure |
Gets information about role assignments in Azure AD. |
| Get-Azure |
Gets information about role definitions in Azure AD. |
| New-Azure |
Creates an Azure AD role assignment. |
| New-Azure |
Creates an Azure AD role definition. |
| Remove-Azure |
Removes a role assignment. |
| Remove-Azure |
Removes a role definition. |
| Set-Azure |
Update a role definition. |
While we are still on the topic of roles/permissions, the Azure AD Privileged Identity Management module has now been assimilated into the AzureAD module, meaning we can use the corresponding cmdlets to manage PIM roles and assignments for Azure AD roles and Azure RM resources. Well technically, you can only manage the Azure RM ones, as the Azure AD roles are still in the process of being moved to the new model. FWIW, creating a new Azure AD role assignment via the New-AzureADPrivilegedRoleAssignment cmdlet worked just fine for me, so you can expect full support for Azure AD roles in the coming weeks/months. Until then, here are the articles with details on each of the Azure RM PIM cmdlets:
| Add-Azure |
Use this API to add a new azure AD MS privileged resource. |
| Close-Azure |
Cancel a AzureADMSPrivilegedRoleAssignmentRequest |
| Get-Azure |
Get azure AD MS privileged resource |
| Get-Azure |
Get role assignments for a specific provider and resource |
| Get-Azure |
Get role assignment request for a specific resource |
| Get-Azure |
Get role definitions |
| Get-Azure |
Get role settings |
| Open-Azure |
Create a role assignment request |
| Set-Azure |
Update a role assignment request |
| Set-Azure |
Update role setting |
And the corresponding articles for the Azure AD PIM cmdlets:
New-AzureADPrivilegedRoleAssignment
Get-AzureADPrivilegedRole
Get-AzureADPrivilegedRoleAssignment
And in the last versions of the modules, released post-Ignite, the following set of cmdlets has been introduced:
- Add-AzureADMSServicePrincipalDelegatedPermissionClassification
- Get-AzureADMSApplicationTemplate
- Get-AzureADMSPasswordSingleSignOnCredential
- Get-AzureADMSServicePrincipalDelegatedPermissionClassification
- New-AzureADMSPasswordSingleSignOnCredential
- Remove-AzureADMSPasswordSingleSignOnCredential
- Remove-AzureADMSServicePrincipalDelegatedPermissionClassification
- Set-AzureADMSPasswordSingleSignOnCredential
The *-AzureADMSServicePrincipalDelegatedPermissionClassification cmdlets seem to deal with the new concept of assigning “classifications” to service principal objects associated with Azure AD applications. More specifically, the classification is basically a tag on any of the delegate permissions granted on/requested by the service principal, which seem to be used to indicate the potential impact that granting the corresponding permissions can have. Three values are currently supported: “Low”, “Medium”, “High”.
The *-AzureADMSPasswordSingleSignOnCredential cmdlets allow customers to manage the credentials for Password SSO applications, while the Get-AzureADMSApplicationTemplate cmdlet can be used to list applicationTemplate objects from the AzureAD Gallery or the App Marketplace.
Lastly, a bunch of cmdlets dealing with Azure AD B2C policies have been added. Note that for any of these to work, you need to be connected to the corresponding Azure AD B2C instance!
| Get-Azure |
This cmdlet is used to retrieve the created trust framework policies (custom policies) in the directory. |
| New-Azure |
This cmdlet is used to create a trust framework policy (custom policy) in the directory. |
| Remove-Azure |
This cmdlet is used to delete a trust framework policy (custom policy) in the directory. |
| Set-Azure |
This cmdlet is used to update a trust framework policy (custom policy) in the directory. |
When it comes to parameter changes, the following can be mentioned:
- The –CompanyName parameter has been added to the Set-AzureADUser cmdlet and the corresponding property is returned in the output of Get-AzureADUser.
- The –Filter parameter has been added to the Get-AzureADDirectoryRole cmdlet.
- The –IsDefaultForCloudRedirection parameter has been added to the New-AzureADDomain and Set-AzureADDomain cmdlets.
- The –IsAssignableToRole parameter has been added to the Get-AzureADMSGroup and New-AzureADMSGroup cmdlets in preparation for supporting group-based role assignments.