Over the last few weeks, some reorganization has happened in the Azure AD blade in the Azure portal, and some of the settings have been moved around. Some new settings have also appeared, so let see what’s changed.
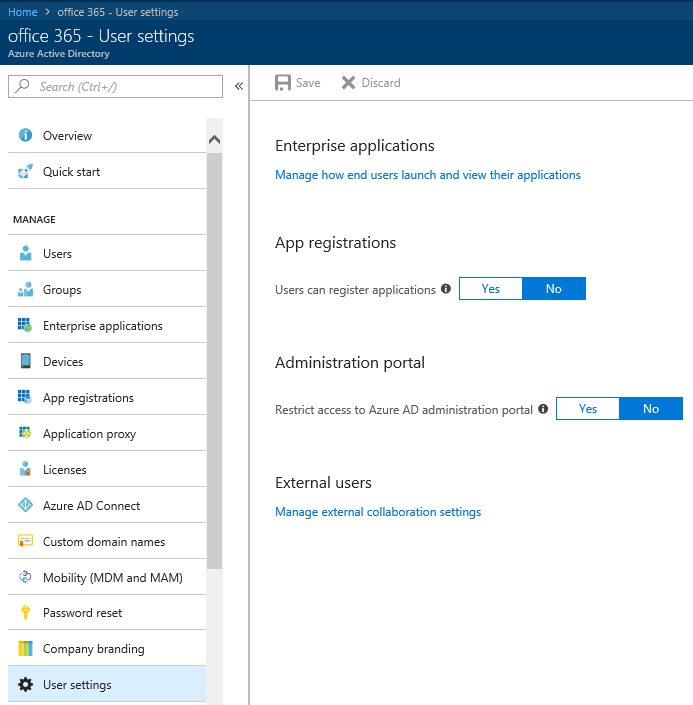
If you navigate to the User settings tab, you will see that it’s barren now, with most of the settings moved to their own pages. Here’s what the current version looks like:
The only settings left on this page are the “Users can register applications” toggle and the “Restrict access to Azure AD administration portal” one, as shown above. All the other app-related settings have been moved under the Enterprise applications tab, and we will talk about them in a minute. First, lets cover one of the major changed, and a welcome addition – the External users controls.
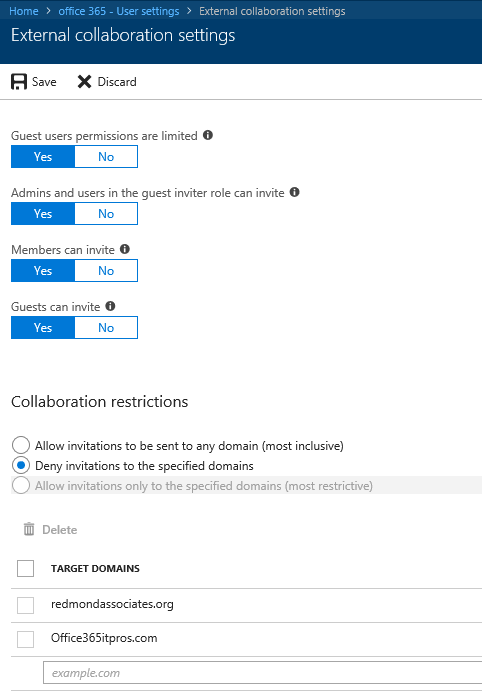
At the top, you will see the familiar Guest control settings, such as limiting Guest permissions or limiting invitations:
A new group of settings will be visible under Collaboration restrictions. You can granularly control the list of external domains from which Guest users can be invited, by selecting the setting most suitable for your organization and populating the Target Domains list. Those settings were previously only configurable via the Azure AD (Preview) PowerShell module and the *-AzureADPolicy cmdlets, as detailed here: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-b2b-allow-deny-list#set-the-allow-or-deny-list-policy-using-powershell
It’s worth mentioning that those are not the SharePoint/ODFB settings, but the new service-wide controls which we first discussed over at the MTC. I’m relieved to see Microsoft listening to our feedback and providing UI controls for those settings, rescuing us from having to deal with the crappy JSON-based format used by the cmdlets.
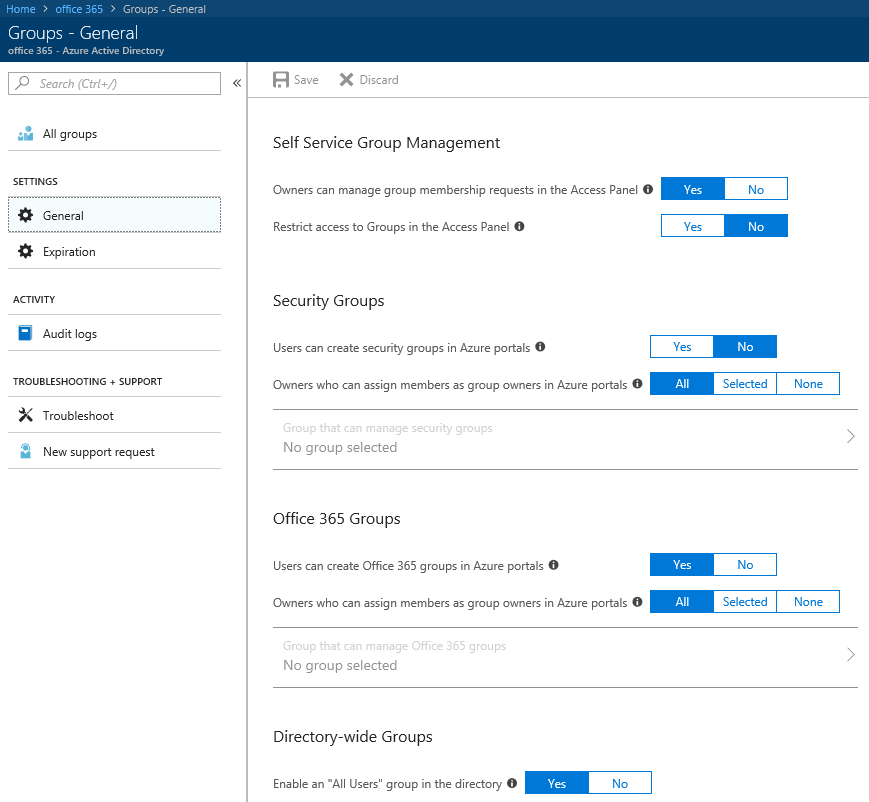
Moving away from Users, the Group settings have also been reorganized a bit. We now have two pages, General and Expiration settings. On the General page, you can find the familiar controls to restrict Security and Office 365 Groups creation and management, as well as the self-service related settings. Here’s how it looks like:
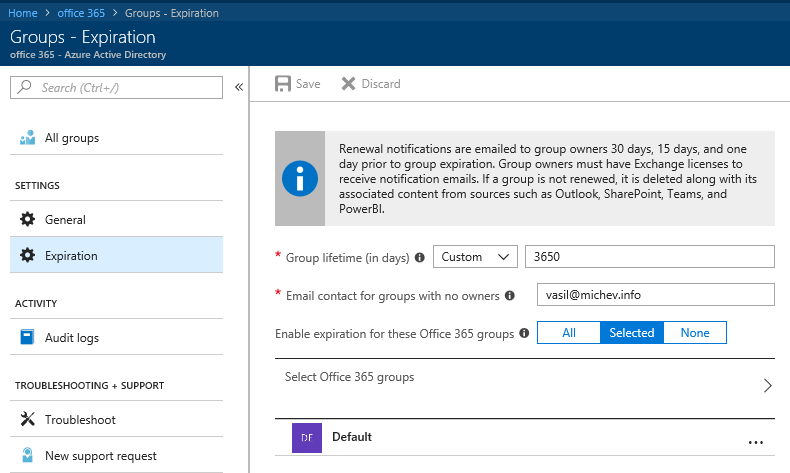
On the Expiration settings page, you can find all the controls related to the Groups expiration feature, which we first discussed almost an year back.
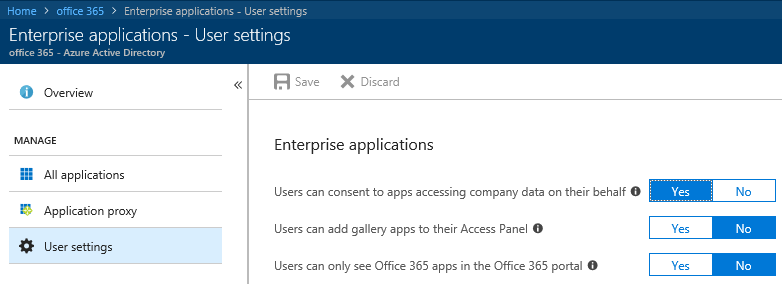
Moving on to the Enterprise applications tab, you will find the corresponding Application-related User settings section. Those include the option to Consent to apps, use the self-service feature for password-SSO apps and to see Azure AD-integrated apps in their Office 365 launcher. Here’s how the settings look like:
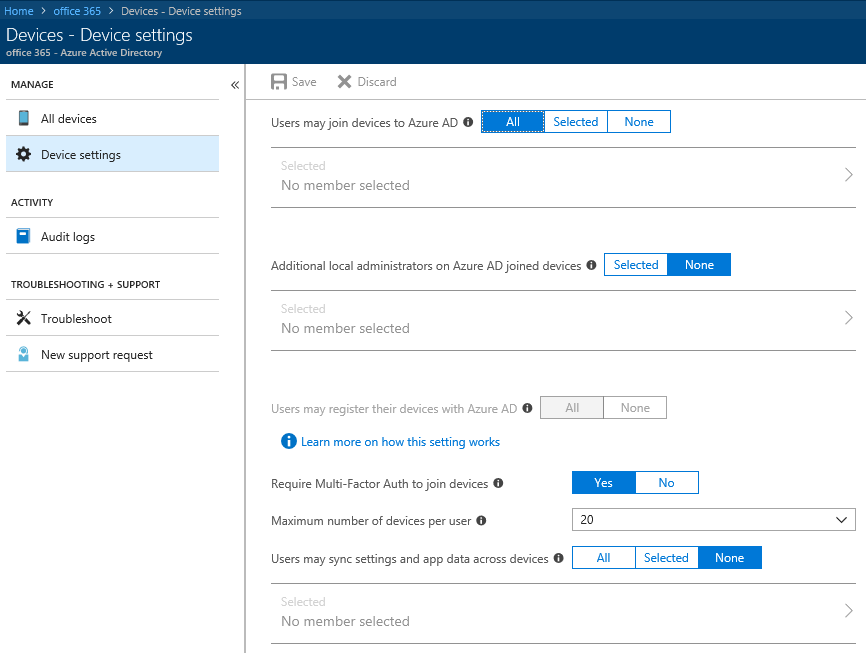
To complete the list, here’s how the Device settings look like:
That’s it for now, I’ll try to keep the article updated as new changes are rolled out.