So Ignite is over and now it’s time to catch up on all the cool new Office 365 and Azure AD features announced or showcased. One such cool feature is the ability to configure custom idle session timeout window for SharePoint Online, as showcased in this session: https://youtu.be/1vnGXvjOm98?t=911
To configure the feature, you will need the latest version of the SharePoint Online Management Shell PowerShell module, which you can download here. Yes, it’s only configurable via PowerShell for the time being, by means of the Set-SPOBrowserIdleSignOut cmdlet. Here’s an example:
Set-SPOBrowserIdleSignOut -Enabled $true -WarnAfter (New-TimeSpan -Seconds 30) -SignOutAfter (New-TimeSpan -Minutes 1)
To check the settings, use:
Get-SPOBrowserIdleSignOut Enabled WarnAfter SignOutAfter ------- --------- ------------ True 00:00:30 00:01:00
Once configured, any user that access a SharePoint Online resource will be subject to the new timeout, regardless of permissions, network location, device and so on. The only factor that has impact on this particular feature is the “Keep me signed in” checkbox. If it was ticked during login, you will be able to use SPO as usual. If the KMSI checkbox was not ticked, then you will be subject to the newly imposed restrictions.
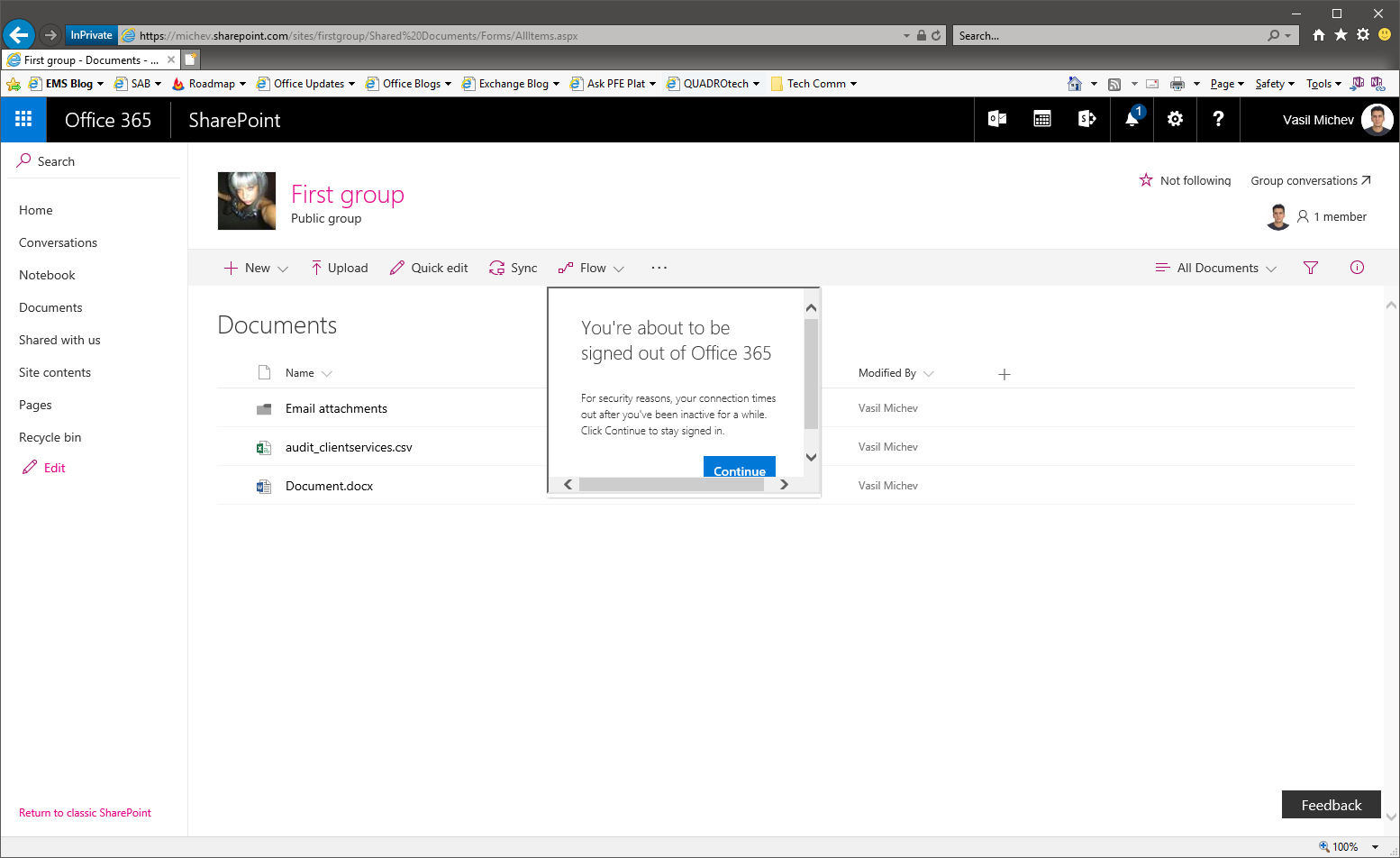
Here’s how the end user experience will look like. If I configure the setting and navigate to any SharePoint Online site (a Group site in this example) and leave the window inactive for a while, I will be presented with the following warning:
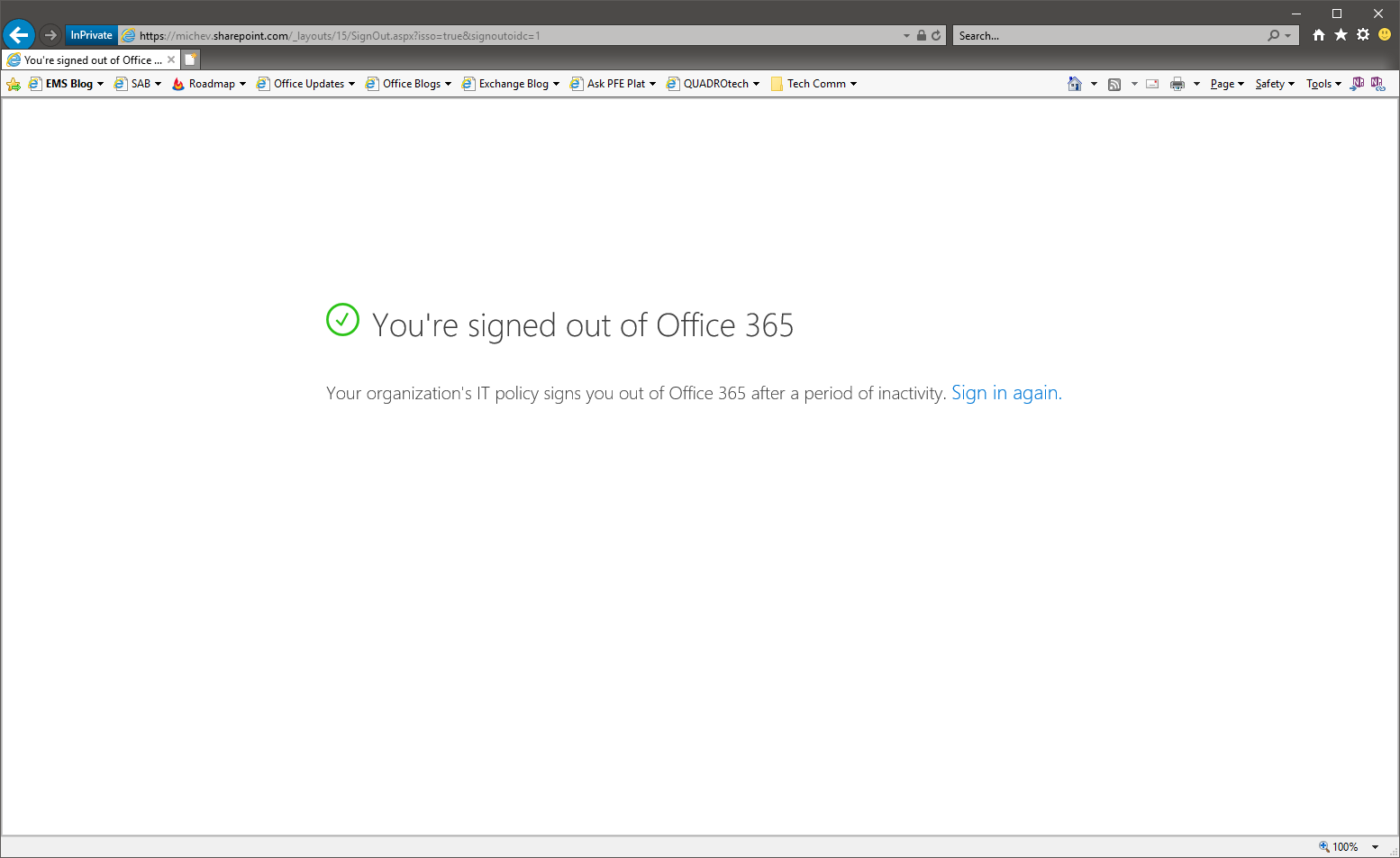
Yes, it’s ugly, I know. But it gets the job done. If I press the continue button, I can continue working until the next time I leave the device idle for the warning period specified when configuring the feature. If I don’t do anything and the signout threshold is reached, I will be automatically redirected to the sign out page:
As mentioned already, this applies to all sessions, regardless of user, location or device. In fact, the above screenshots are taken with my global admin account. Only if you *did not* select the “keep me signed in” checkbox when logging in however. So the question then is, how can I make sure that my users cannot click this checkbox when logging in from shared devices?
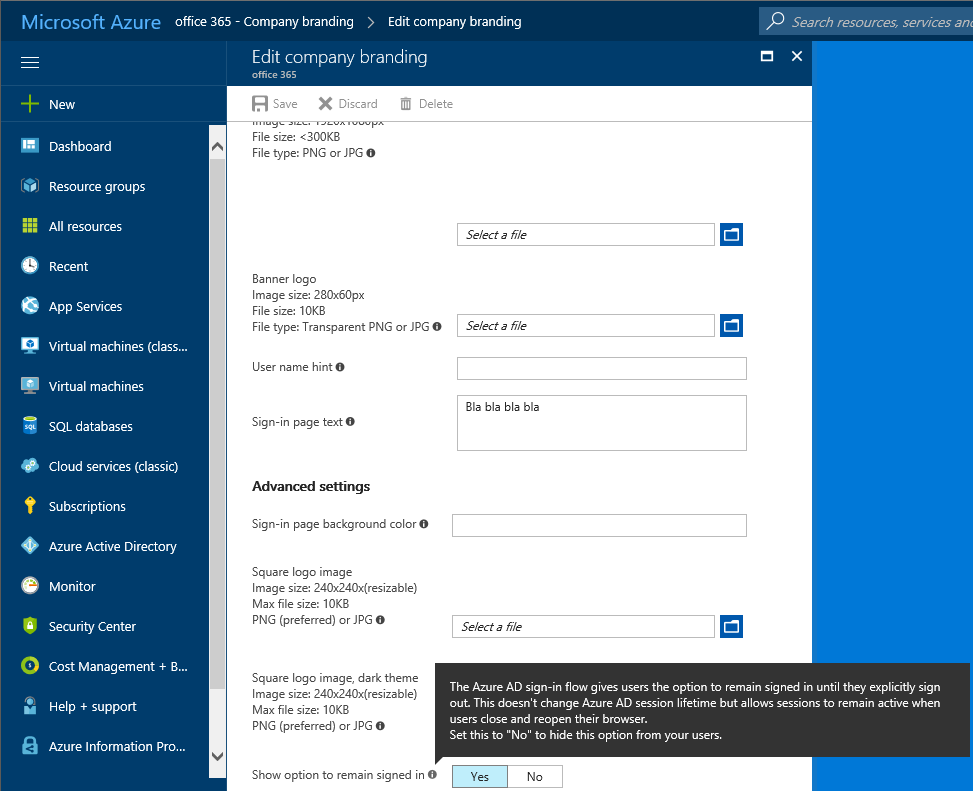
You can prevent the “Keep me signed in” checkbox from being displayed by customizing the Azure AD branding: navigate to the Azure AD blade, select the directory in question, click on Company branding, create a new configuration or edit the existing one, then set the “Show option to remain signed in” toggle to No. Detailed instructions here.
But again we have a similar issue, as the branding changes will apply to all login attempts, regardless of user, location or device. One way to get around this is to use smartlinks, if you are in a federated scenario that is. You can simply add the “loginoptions” parameter to your smartlink and ensure that every login attempt using that link will not only be seamless SSO experience, but also will not be a subject to the idle controls configured above. If you need more info about smart links, check out this article.
Can this be enabled at the site level instead of tenant level?
Can different Idle timeout settings be configured for SPO separate from One Drive? For example, we want OneDrive to be set to 288800, but SPO to 3600?
Unfortunately no, not at this time at least. I’ve seen many people asking for some granularity on this, so perhaps Microsoft will deliver something.
Can you apply different timeout lengths based on a site classification? Like HR sites have a shorter idle limit of 1 min and sales sites have a limit of 30 min?
Not in the initial release, although this feedback was brought several times already, and you can put yours at https://sharepoint.uservoice.com/. Of course, I cannot speak on behalf of Microsoft, so I don’t know whether they will actually release this.