Modern authentication, ADAL or MFA are all different things, but often used to designate the same scenario – using additional authentication factor when logging in to Office 365. Generally speaking, the added security is a great thing, especially important for any privileged accounts. The different teams at Microsoft however have been very slow to adopt this new trend, and Office 365 administrators had to make compromises with security, simply because some of the modalities did not support Modern authentication.
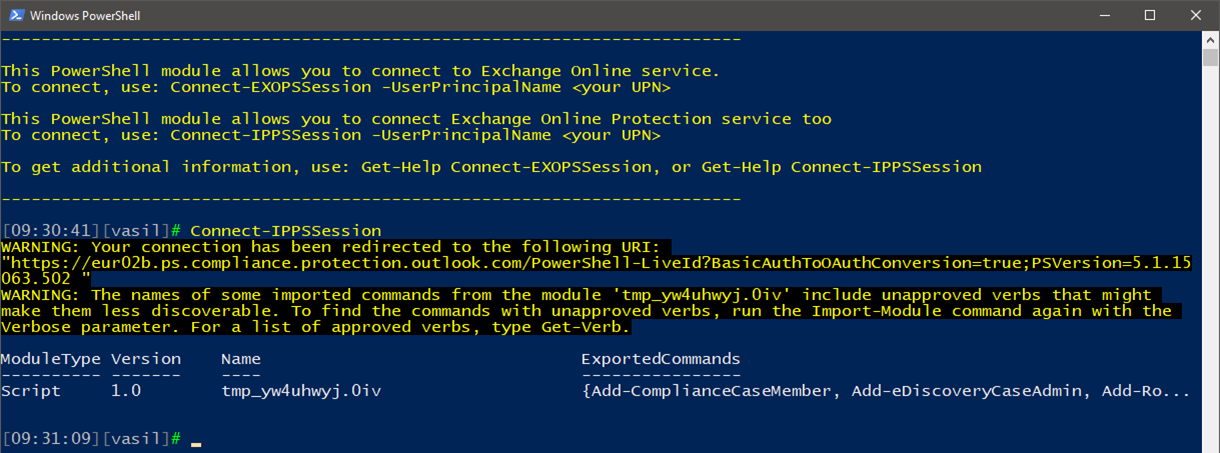
Well, slowly but surely the different PowerShell modules have been updated and now we finally have MFA support for the Security and Compliance Center (aka Protection Center) PowerShell cmdlets as well. It is delivered as part of the new, MFA-enabled Exchange Online PowerShell module, which I blogged about almost an year ago. Those of you that have used the ExO PowerShell module know that it’s delivered as click-once application, which updates automatically, and might have noticed that the latest version introduced a new cmdlet, namely Connect-IPPSSession.
The cmdlet is a simple wrapper function that gets an authentication token from Azure AD and passes it to the New-PSSession cmdlet in order to create a new remote PowerShell session to the Security and Compliance Center endpoint, https://ps.compliance.protection.outlook.com. Which means, you can simply do the steps yourself, following the approach I outlined here.
Or, simply use the shortcut you get on your desktop after installing the tool. You can download it from the Exchange Admin Center, Hybrid tab, or directly via http://aka.ms/exopspreview. Here’s how a connected session will look like:
So there you have it, the SCC PowerShell module is the last to get support for Modern authentication, which in turn means there are no reasons left to not protect all your administrative accounts with Azure MFA or any other form of multi-factor auth!
How can make a REST call to SCC for example to get the same as the Get-DlpCompliancePolicy ?
There are no direct endpoints for that. The latest (preview) version of the module however uses the InvokeCommand method, much like the ExO cmdlet. See https://www.michev.info/blog/post/3883/exchange-online-powershell-module-gets-rid-of-the-winrm-dependence
Can one configure PowerShell to always use MFA? I know I can use different PS enabled for PS, but that leaves the choice to an admin (or bad actor). Can I enforce a config that prevents access (at the o365 layer) unless MFA is used (for PowerShell)?
You can now use Conditional Access policies to block any form of legacy auth: https://www.michev.info/Blog/Post/2130/blocking-legacy-authentication-in-office-365
The first one is just a Warning, that’s expected and is common with many modules, including the ExO one.
Get-AtpPolicyForO365 is actually an Exchange Online cmdlet, you don’t need to use the SCC module to get it. So is Get-PhishFilterPolicy and the others that relate to antispam/antiphish/ATP. Just use the ExO module for those.
I notice you receive the same error we are when doing this:
“The names of some imported commands from the module x include unapproved verbs that might make them less discoverable etc”
We’ve also noticed that some of the commands are missing, such as Get-AtpPolicyForO365 and any to do with Anti-Phishing… have you discovered that too?