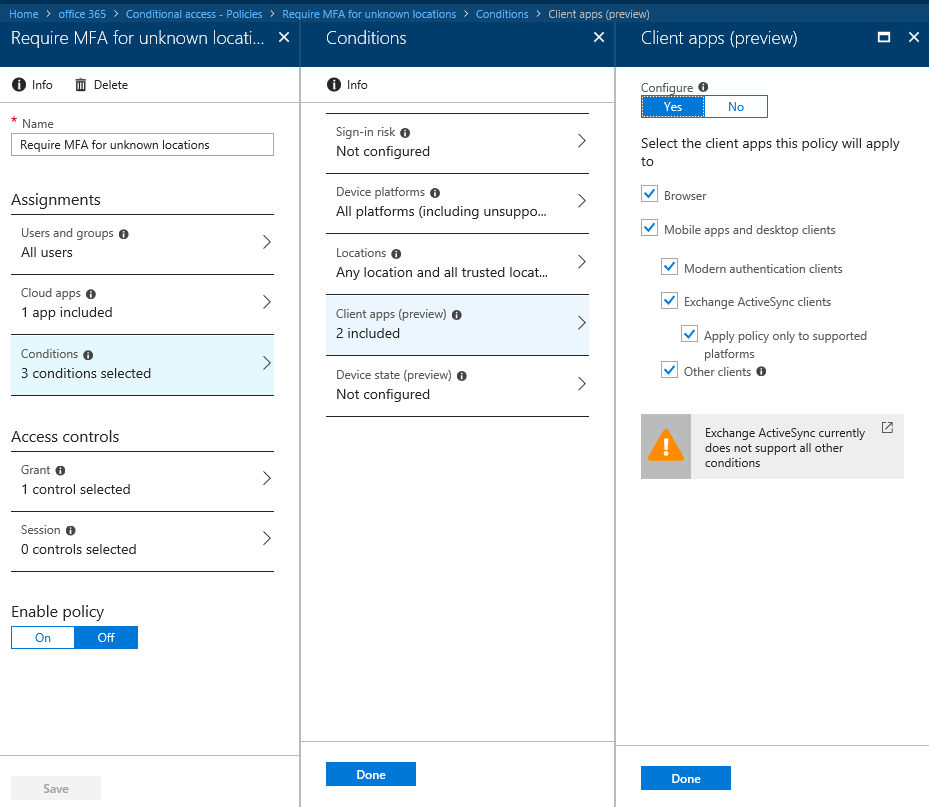
Finally, we are able to block users and applications from using legacy authentication protocols to access Office 365. This is made possible thanks to the improvements made in Conditional Access, namely the new “Other clients” condition that is currently in Preview.
Unlike other CA conditions, the “Other clients” condition can only enforce the “block access” control. Technically, it can still be configured with any of the controls supported by Conditional Access, however the only control that will actually work is “block access”. This is because none of the other controls have support for legacy authentication and all of them depend on Modern authentication to work correctly.
The below picture illustrates how to get to and configure the new condition. Basically, open any existing CA policy or create a new one, click the Conditions entry on the left, click Client apps, select the Mobile apps and desktop clients checkbox and select the Other clients entry. Adjust any other conditions as necessary.
Note that this is just an example, in a real-world scenario you probably want to have a separate policy that blocks legacy authentication in addition to a regular one that enforces MFA for any client supporting Modern authentication.
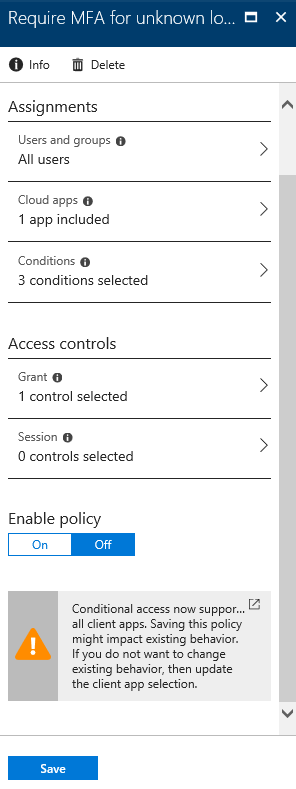
Before saving the policy, you will be warned about the possible impact it might have:
For additional information, you can consult the official documentation: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-conditional-access-conditions#legacy-authentication
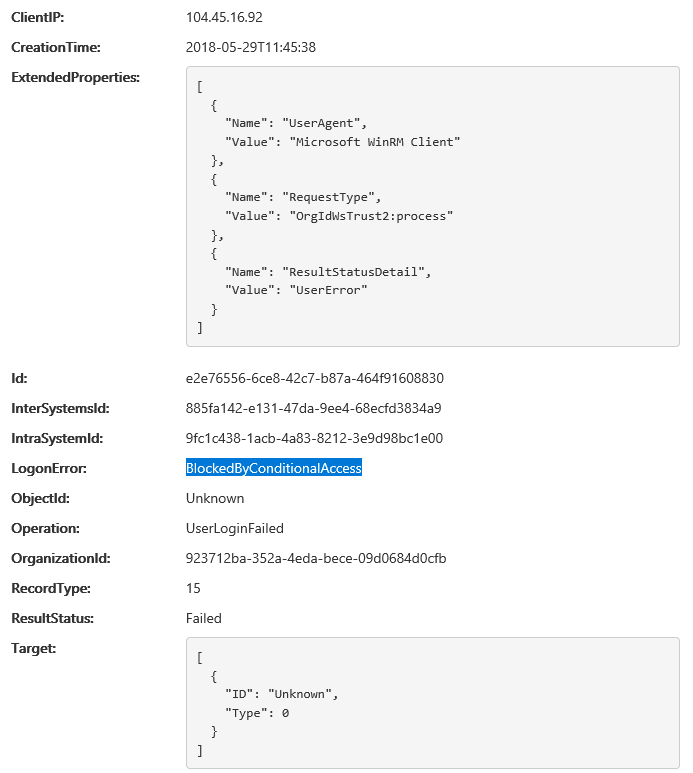
As noted in the documentation, it might take up to 24h for the changes in the CA policy to apply. In my tests, Exchange-related functionalities such as Autodiscover, EWS or PowerShell access were blocked almost immediately, while access to MSOnline via legacy authentication continues to work. With some delay, some entries that show the blocked or successful authentication have appeared in the Audit logs, for example:
I will continue monitoring the effects of the policy and update the article with additional information later on.
In any case, this is one of the biggest addition to the service in a while and will surely help beef up security for any organization using Office 365. Go ahead and adjust your CA policies right away!
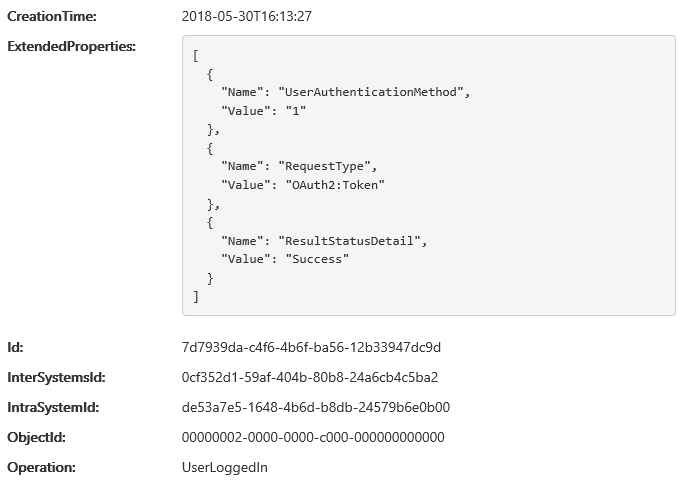
Update: Turns out the MSOnline module will use Modern authentication even in (some) situations where the old, non-ADAL credentials prompt is presented. More specifically, when using cloud-only account with no MFA enabled (either via MFA or CA policy), the OAuth 2.0 Resource Owner Password Credentials Grant will be used. This can also be confirmed by looking at the audit log events corresponding to these login attempts:
So, rest assured, the “block legacy auth” policy works as expected even for the MSOnline module!