A new functionality has appeared over at the Office 365 Security and Compliance Center, namely a UI-driven method for submitting messages that made it past the various EOP layers and into user’s mailboxes. Found under the Threat management -> Submissions tab, and accessible directly via https://protection.office.com/reportsubmission, the page looks very similar to the Threat Explorer itself. Actually, if you select the newly added Submissions option under the View dropdown in Threat Explorer itself, you will be presented with the exact same UI seen on the Submissions page, so it’s a bit puzzling why Microsoft decided to duplicate this. Perhaps to make it easier to discover the submission tool.
Anyway, to report a false-positive or false-negative message to Microsoft, press the New Submission button on top. You will be presented with the New submission pane, where you need to select the type of submission (Email, URL or attachment) and provide some additional details. For an Email type submission, you can directly point to the Network Message ID, which is a very convoluted way of saying “the GUID of a message trace you’ve run that lists the corresponding message”. My initial expectations were for a MessageID, however the example value populated in the field is in GUID format, so definitely not a MessageID. So I went ahead and run a message trace for one of the spam messages that made it to my Inbox (sadly I see a big increase in those lately):
Get-MessageTrace -SenderAddress no-reply@notices.yola.com | fl Message Trace ID : 0ac9b5cf-9e62-4f69-6325-08d706be7a9a Message ID : <2121197565.5791741562931944839.JavaMail.app@rapp43.atlis1> Received : 12/07/2019 11:45:46 Sender Address : no-reply@notices.yola.com Recipient Address : vasil@michev.info From IP : 74.112.67.187 To IP : Subject : fgagag it's time to start building your website. Status : Delivered Size : 135540
Providing the Message trace ID value from above did the trick, and after a short validation the value was accepted. Next, I had to provide a Recipient, which I was able to select from the automatically populated drop down list (nice touch!). After that, one must specify the Reason for submission, in other words whether you are reporting a false-positive or false-negative item. Lastly, select the Item type: Spam, Phishing or Malware. In my case, the submission looked like this:
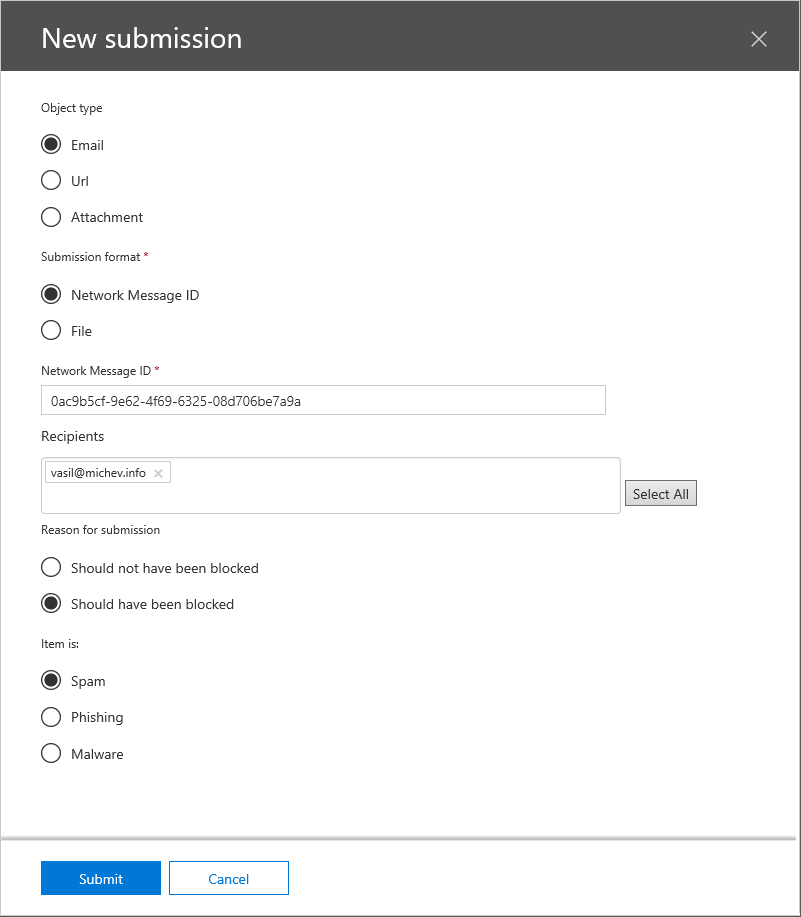 Alternatively, one can provide a sample of the message in .eml format, instead of pointing to a network trace id. Why only .eml is supported is beyond me, given Outlook cannot natively save messages to this format. Apart from reporting messages, one can use the tool to submit URLs or Attachments as well. The UI used for those is similar to the above, with some of the unnecessary controls removed.
Alternatively, one can provide a sample of the message in .eml format, instead of pointing to a network trace id. Why only .eml is supported is beyond me, given Outlook cannot natively save messages to this format. Apart from reporting messages, one can use the tool to submit URLs or Attachments as well. The UI used for those is similar to the above, with some of the unnecessary controls removed.
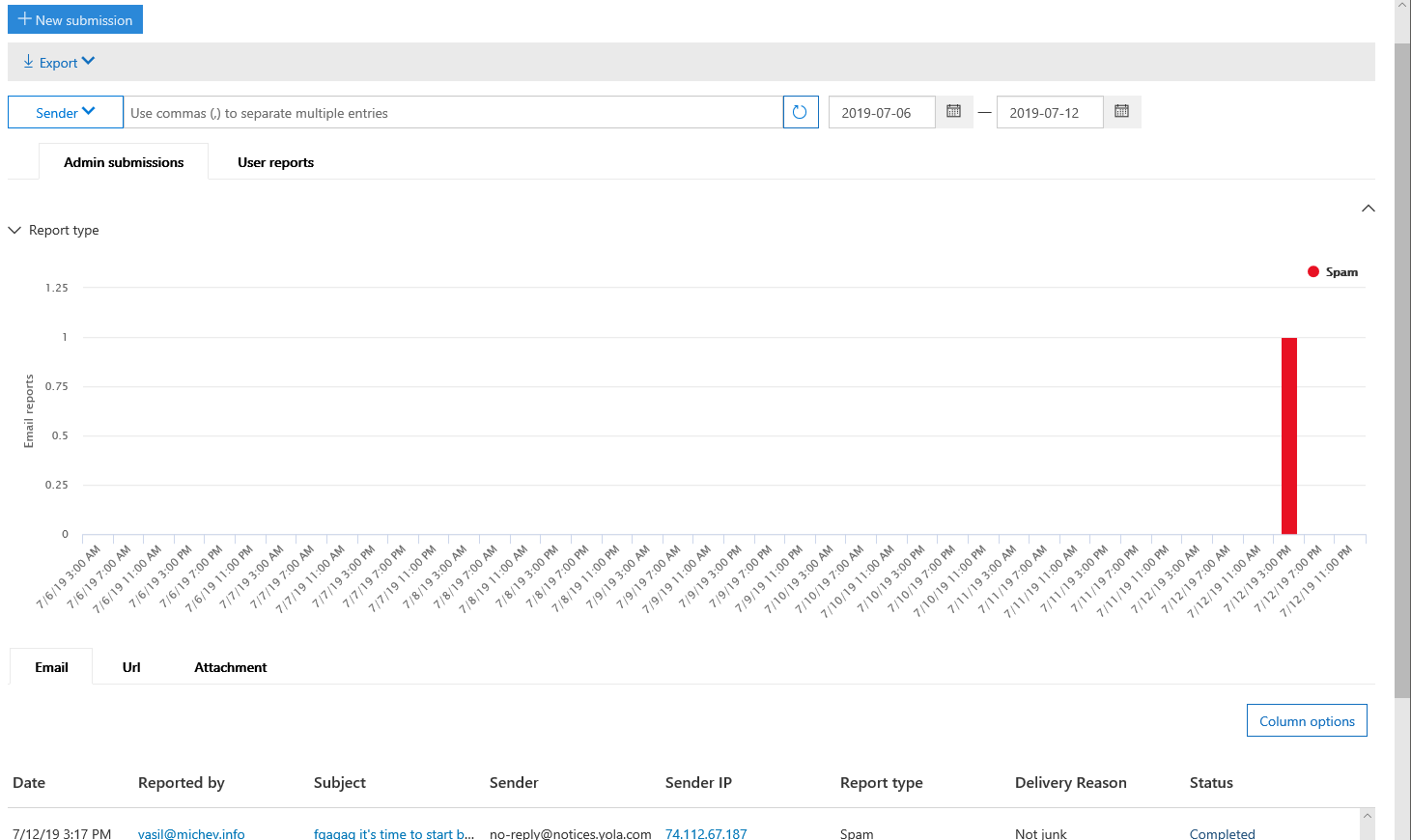
After you submit a message, an entry will appear in the Report section, where submissions from the last week will be visualized as a Graph. Again, the UI here is pretty much a copy of the Threat explorer UI, so you might already be familiar with it. A separate tab (and graph) is available for any user-submitted messages (via the Outlook or OWA add-ins). Item-level details can be obtained from the corresponding Item tab below, grouped under Email, Url, Attachment respectively. Clicking a particular entry will bring up the right pane with some additional details, including the result of the scan performed.
 In my case, the verdict was that the item in question was not spam, which fills me with confidence about the effectiveness of the process of evaluating user- and admin-submitted items. Still, it’s nice to have an UI-based method to do this, as well as a way to check the status. The old method of submitting messages directly to email should still work as well.
In my case, the verdict was that the item in question was not spam, which fills me with confidence about the effectiveness of the process of evaluating user- and admin-submitted items. Still, it’s nice to have an UI-based method to do this, as well as a way to check the status. The old method of submitting messages directly to email should still work as well.
Is there a way (or need?) to bulk submit messages? When phishing messages get through EOP/ATP they invariably are sent to many users, but each users mail has a different network message id. If the messages are exactly the same except for the recipient do all examples need submitting or is it enough to just submit one example?
Does submitting a message that should have been blocked initially have any impact on Zero-hour auto purge regarding reported message?
Supposedly they look at each message, it’s also supposedly used to train the ML models, etc. Personally I’ve seen a very noticeable increase in the amount of spam/bulk messages hitting my mailbox, so mixed feelings on that one 😉