While application extensibility is great thing to have in general, and certainly one of the factors that have contributed to Microsoft’s success over the years, it can also cause some unpleasant issues when left unchecked. Take for example the good old VBScript – insanely powerful and a very useful tool for every system administrator, turned into an easy to abuse attack vector. And that’s just one of many examples.
Office 365 is not an exception in this, and we have already seen some attempts to leverage the Azure AD application model for gaining access to company’s data. It’s thus understandable that some companies have a very strict policy when it comes to any extensibility feature. On the other hand, the different teams at Microsoft are sometimes eager to showcase their new product or feature, which more often than not results in a “enabled by default” approach. Microsoft Teams also follows this model and an alarmingly long list of Bots and Connectors was made available from the get go.
Now, finally, we are able to control those settings down to the individual connector level, as well as configure a default behavior for any newly released connectors. Here’s how to do that.
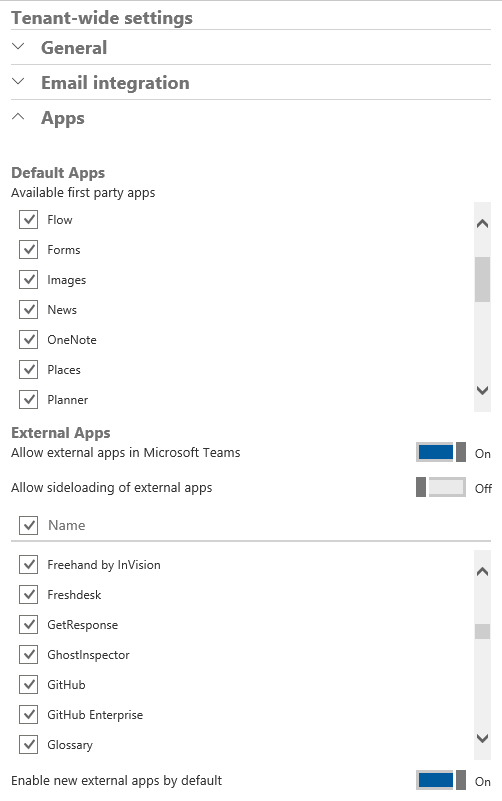
To access the settings, navigate to the Office 365 Admin portal, expand the Settings menu on the left and click Services and Add-ins. Scroll down to the Microsoft Teams entry and click on it. Under the Tenant-wide settings group, expand the Apps item. The below screenshot illustrates the relevant settings, which will probably move to the new Teams admin center over time:
The Default Apps section covers any first-party (Microsoft) apps that integrate with Teams. Those include SharePoint Online, Yammer, Planner and more. While such applications should be safe to use in general, a newly released application might not conform to all data governance requirements or might store data in rest in another location, which in turn might prove prohibiting for its use. Thus it’s a good thing to have this list exposed, even though Microsoft is a bit slow to update it at times (for example the Stream entry is still not added to the list).
The External apps section is the place where you can configure restrictions on any third-party apps that integrate with Teams. If you need to, you can globally turn off access to all such apps via the Allow external apps in Microsoft Teams toggle. This setting will apply to all Teams in the tenant, although it is independent from the similar setting that can be controlled for Office 365 Groups. In addition, we still have the option to control this on a per-team basis by running the Set-UnifiedGroup cmdlet against the underlying Office 365 Group object.
To control access on a per-app basis, use the long list control visible in the middle of the section. Each and every Connector used by Teams (or Groups) should be listed here and can be toggled on/off as needed. Clicking the checkbox on top, next to the Name label will select all entries, and clicking it again will deselect them all, allowing you to quickly toggle the status of all apps. You can of course toggle them one by one as well. In addition, the Enable new external apps by default toggle will ensure that newly released apps/connectors are enabled or disabled by default, respectively. Lastly, the Allow sideloading of external apps toggle allows us to control access to the functionality to upload a custom app, as in an app not found in the Teams Store.
That’s pretty much all there is to the process of controlling application access with Teams. The new granular controls are surely a welcome addition and one can only hope that Microsoft will keep the list current, as well as not try to force any additional “enabled by default” features, without providing the relevant options to disable them.
No longer Valid for O365 Admin Portal. Settings shown are not available. Please update for current configuration