This is hardly news by now, as it has been available for several months already, but in case you missed it – the Exchange Online PowerShell module now support the -Credentials parameter. In other words, you can pass a PSCredential object to it, just like you would do with the “regular”, non-MFA enabled ExO PowerShell remoting. Here’s how:
$cred = Get-Credential user@tenant.onmicrosoft.com Connect-EXOPSSession -Credential $cred
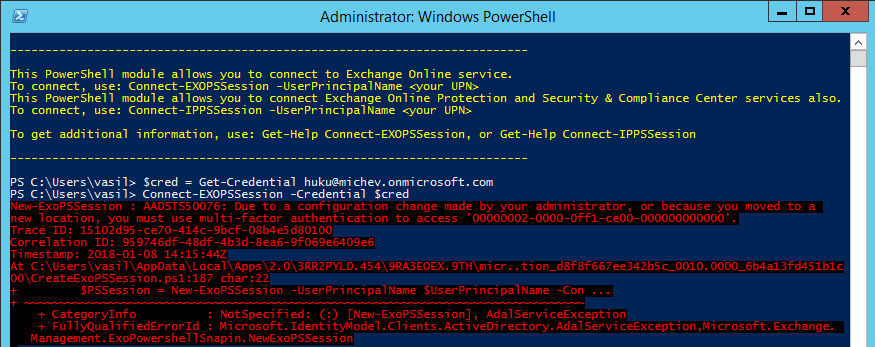
What’s even better, passing Credentials does not bypass modern authentication, i.e. does not switch to using legacy authentication like some of the other Office 365 related modules do. This has both positives and negatives, the negative being that if you do have any form of multi-factor authentication enabled for the account in question, the login will fail:
On the other hand, it means you can now easily automate connecting via the ExO PowerShell module in your scripts for accounts that do not have MFA enabled. And, the big news here, if you are using Azure MFA and you have configured any of the bypass functionalities, you will now be able to connect automatically by passing the Credentials object. No MFA prompt will be triggered, and no legacy authentication used!
Now, the bad news is that the Security and Compliance Center PowerShell does not yet support this. I know, I know, it’s weird, considering they are practically using the same cmdlets. But as different teams at Microsoft are responsible for the different portals, the SCC cmdlet (Connect-IPPSSession) has not yet been updated with the -Credentials parameter.
Well, you can easily make it available by editing the Connect-IPPSSession function inside the CreateExoPSSession.ps1 script file. I wont go into details on this, as it’s not considered a supported scenario, and anyway the file will be overwritten the next time the click-once application that represents the module is updated. But it’s certainly possible to connect to SCC PowerShell by passing a Credentials object too 🙂