Hopefully this will save few people some time:
Lync 2013 client does NOT work with mandatory profiles when connecting to Lync Online.
I am publishing this post because all the information I was able to find on the internet suggests that Lync will only have issues with conference calls (KB 2552221) or that you will get a specific error message (“There was a problem acquiring a personal certificate required to sign on. If the problem continues, please contact your support team”).
Sadly, this isn’t always the case. What they have not mentioned is that those Lync certificates are mandatory in some cases (especially Lync Online). Long story short, I was asked to assist with Lync installation for the Citrix environment of one of our clients. Regrettably, no one told me that mandatory profiles are being used in that environment and I had to find it the hard way. On top of everything else, Lync was not showing any error message, but was simply displaying the “Connecting” message continuously. A look at the log files showed the same message being recorded repeatedly after the initial register request: SIP/2.0 401 Unauthorized. It wasn’t until I examined the errors on the Trace tab until I noticed a simple “No certificate” error, which ringed a bell. I then confirmed that indeed mandatory profiles are used, which explained the issue.
Here’s a quote from the KB above: This issue occurs when users sign into the Lync client using a Windows Active Directory Domain Services mandatory profile. Mandatory profiles are read-only user profiles. Since changes to the mandatory profile cannot be saved, the design of the Public Key Infrastructure (PKI) functionality does not allow this operation. This causes the creation of the secure keys that are needed for the creation of the focus for the Lync conference to fail.
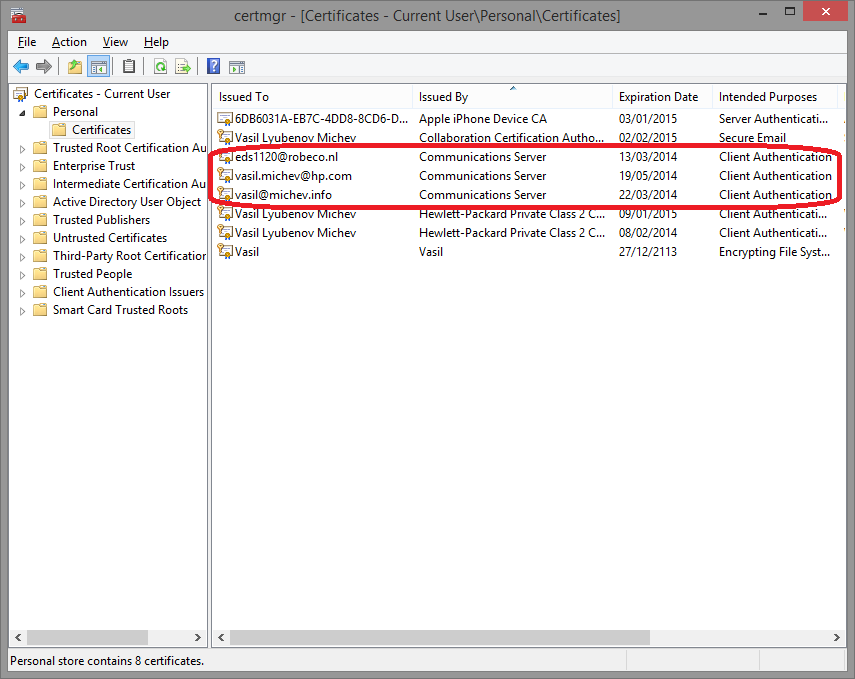
And here is some more info about those “Communication server” certificates: There are three authentication packages available to the Lync client when authenticating a registered endpoint in a Lync environment: NTLM, Kerberos, and TLS-DSK. By default, all Lync clients and Lync telephony devices authenticate against Lync servers using the new authentication package, TLS-DSK. The TLS-DSK authentication package uses an X.509 v3 certificate to authenticate an endpoint. The certificate is a self-signed client authentication certificate issued to the client by Lync Server. This certificate is found in the user’s personal certificate store in their Windows profile. Here is how it looks like in certmgr.msc:
-
Authentication with Lync when Active Directory is unavailable.
-
Ability to use a certificate instead of enterprise credential.
-
Quicker authentication.
-
Numeric Pin authentication.
-
Failover pool authentication during disaster recovery.
After initial authentication and provisioning of a client authentication certificate, the user’s credentials are not requested or presented to the Lync Server system. Subsequent logins to the system utilize the certificate provisioned during initial login. The default certificate validity period is 180 day for Lync On-prem installments, however fort the case of Lync Online, this period is reduced to 32hours.
More info can be found for example here.