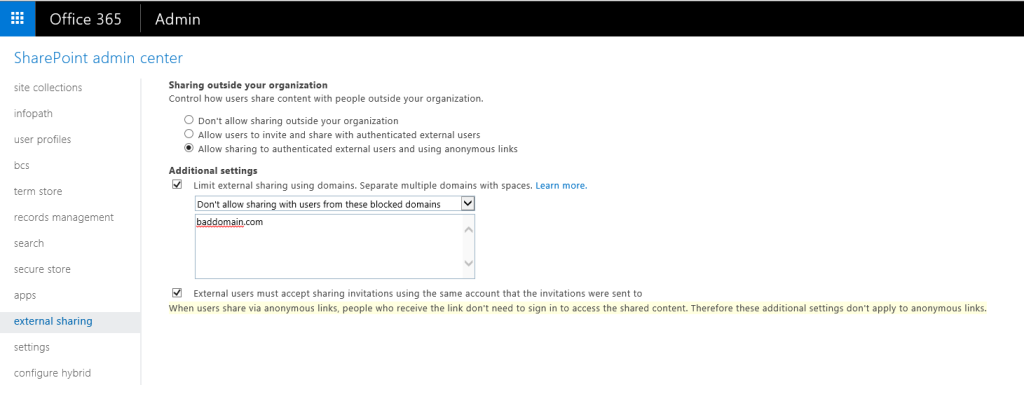
This feature has been long awaited and is finally here: we now have granular control over the External sharing feature in SharePoint Online. The deployment for First Release customers has already started and regular tenants should follow soon. You can access the settings via the Office 365 Admin center -> SharePoint -> External Sharing, or via the direct link: https://tenant-admin.sharepoint.com/_layouts/15/online/ExternalSharing.aspx
Apart from being able to control the availability of the sharing feature on the globally on the tenant level (the settings were moved out of the “Settings” menu and into this one), we can now specify a list of Allowed domains, or a list of Blocked domains, if preferred. Basically, it works very similar to how Federation works in Skype for Business Online – you either allow sharing with all external parties, allow sharing with all but few “bad” domains, or only allow sharing with specific domains. Configuring this is as simple as checking the “Limit external sharing using domains” setting and the corresponding option via the drop down menu. Then, provide a list of domains, separated by spaces. No wildcards are accepted, and the list can only be configured on the tenant level currently (so no specific lists per site collection). For additional instructions, you can refer to the documentation.
And of course, we can also control these settings via PowerShell and the SharePoint Online module. The cmdlet we need is the Set-SPOTenant one, and the relevant parameters are SharingAllowedDomainList, SharingBlockedDomainList and SharingDomainRestrictionMode. For example, to configure a “Deny specific domains only” mode and add the “baddomain.com” to the list of disallowed domains, one can use:
Set-SPOTenant -SharingDomainRestrictionMode BlockList -SharingBlockedDomainList baddomain.com
Multiple domains can be specified as space-separated string. As the Allow and Deny scenarios are mutually exclusive, you cannot use both the SharingAllowedDomainList and the SharingBlockedDomainList in the same cmdlet.
The team has also surfaced the “RequireAcceptingAccountMatchInvitedAccount” attribute in the GUI now. That’s an important settings that makes sure external invitations sent to specific address are only accepted by the intended recipient. With this feature disable, the recipient of such invitation can simply forward it to another address, or distribute it via any other means. The first person that clicks the link will be able to gain access to the shared resource, without any check on his identity. This setting will not protect you in any anonymous sharing scenarios however, as the highlighted message on the screenshot above explains.